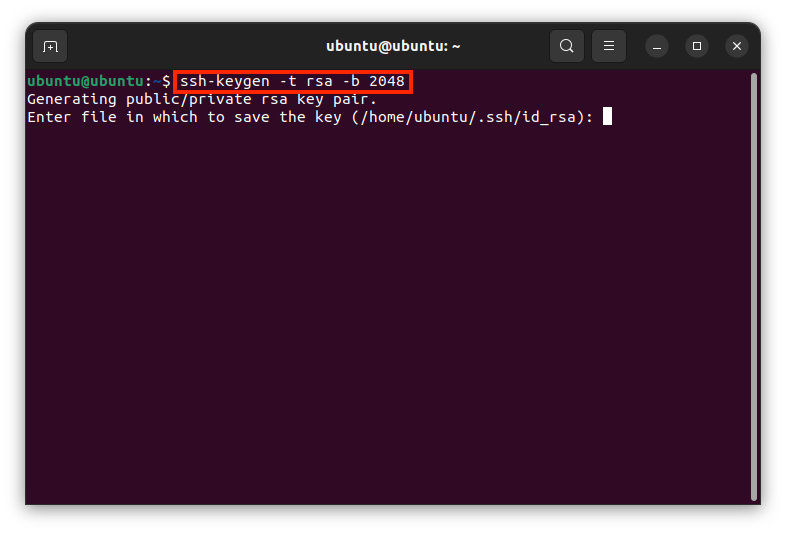
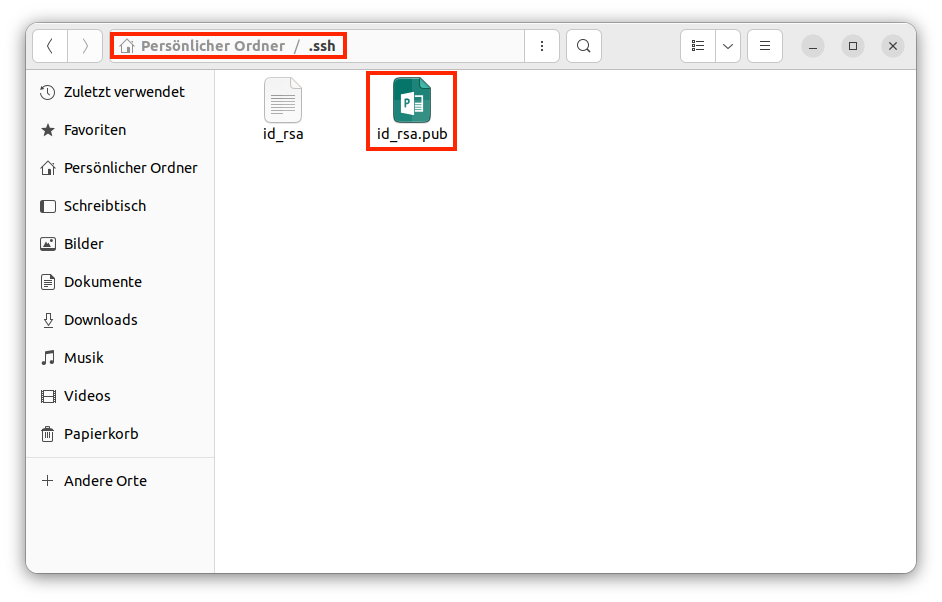
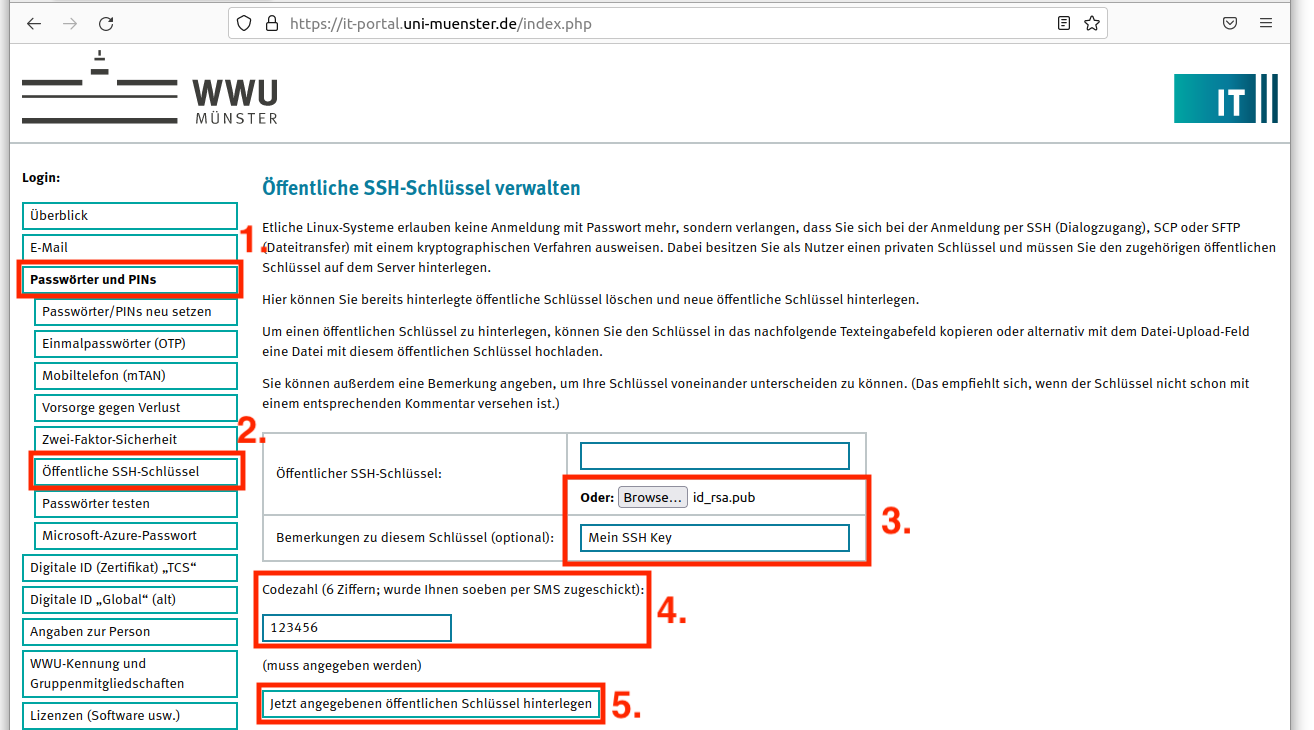
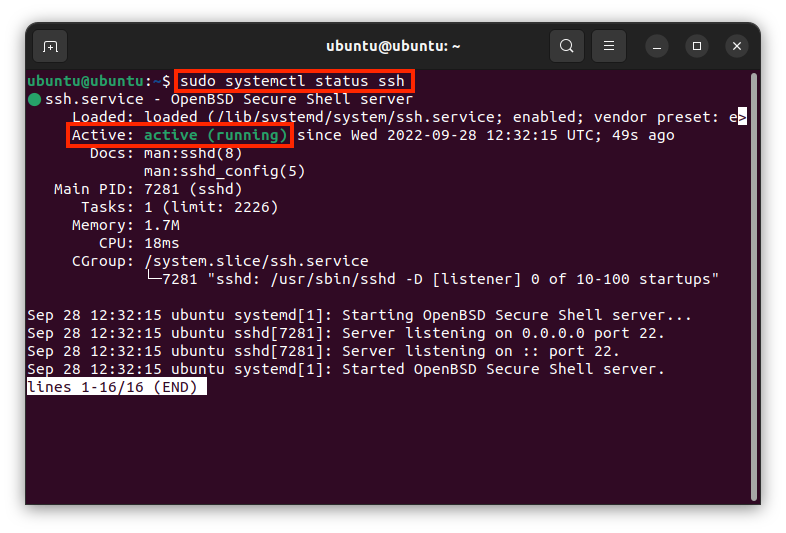
SSH-Jumphost
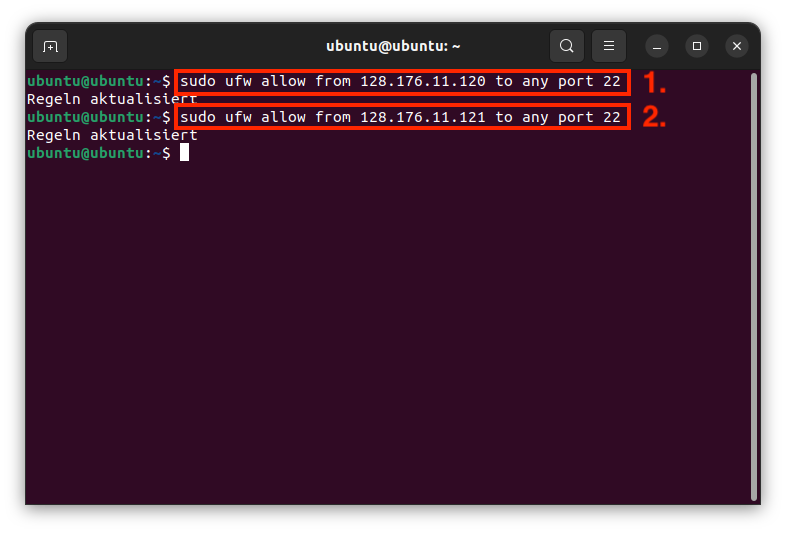
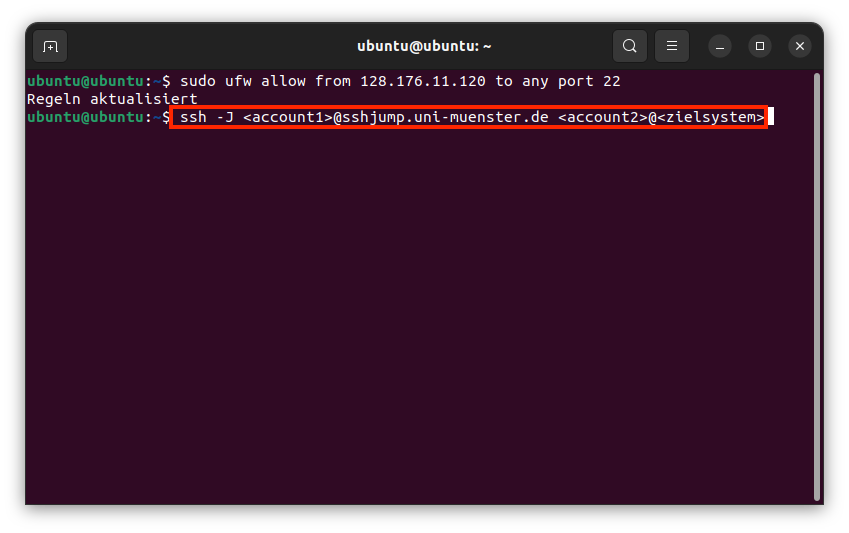
Service: CIT operates a central SSH jumphost cluster. This offers the possibility to access University-internal systems via SSH from outside the university. Both IPv4 and IPv6 connections can be used.
Target Group: students, employees
Usage Costs: free of charge
Contact: Hotline