Please pay attention not only to the pictures in the following instructions, but also be sure to read the introductory explanations and the notes between the individual illustrations thoroughly!
Electronically sign emails
and login to WWW without password
To sign emails electronically, you need a digital ID suitable for this purpose.
In the IT portal, you can obtain such digital IDs from an internationally recognized trust service provider.
Email signatures created with these digital IDs are automatically recognized as valid and signed emails as genuine by all modern email software worldwide.
These digital IDs can also be used to login on the WWW to the web services included in the central single sign-on of the University of Münster without a password.
Furthermore, other email users around the world can send you encrypted emails that only you as the owner of the digital ID can read.(*)
Personal and nonpersonal digital IDs
Digital IDs can be requested only by natural persons that are member of the university or the arts academy.
On the one hand, these persons can request personal digital IDs for themselves. These digital IDs contain the email address and the organizational affiliation and, only if the identity has been sufficiently verified, also the name of the holder and may only be used by the holder personally.
On the other hand, if those persons holds an office, perform a specific function, or are responsible for a well-defined group, those persons may apply for nonpersonal digital IDs for that office or group. These digital IDs contain only the email address and the organizational affiliation and can be passed on to the successor in office or to trusted group members.
Both types of digital ID can be requested in the IT portal under “Digital ID (certificate)”.
Revocations
If a digital ID ever falls into unauthorized hands (is “compromised”), the requesting person is obligated to have the digital ID revoked immediately in the IT portal.
It is also mandatory to revoke digital IDs if information is no longer correct, i.e. name, email addresses or organizational affiliation no longer apply.
The University Certification Authority Münster (UCAM) is entitled and even obliged to revoke digital IDs without prior warning if it learns of such circumstances.
Guides
Please click on the images to enlarge.
Please replace my university ID “perske”, my email addresses, and my further datails with your own data.
Guide: Request a digital ID for emails in the IT portal
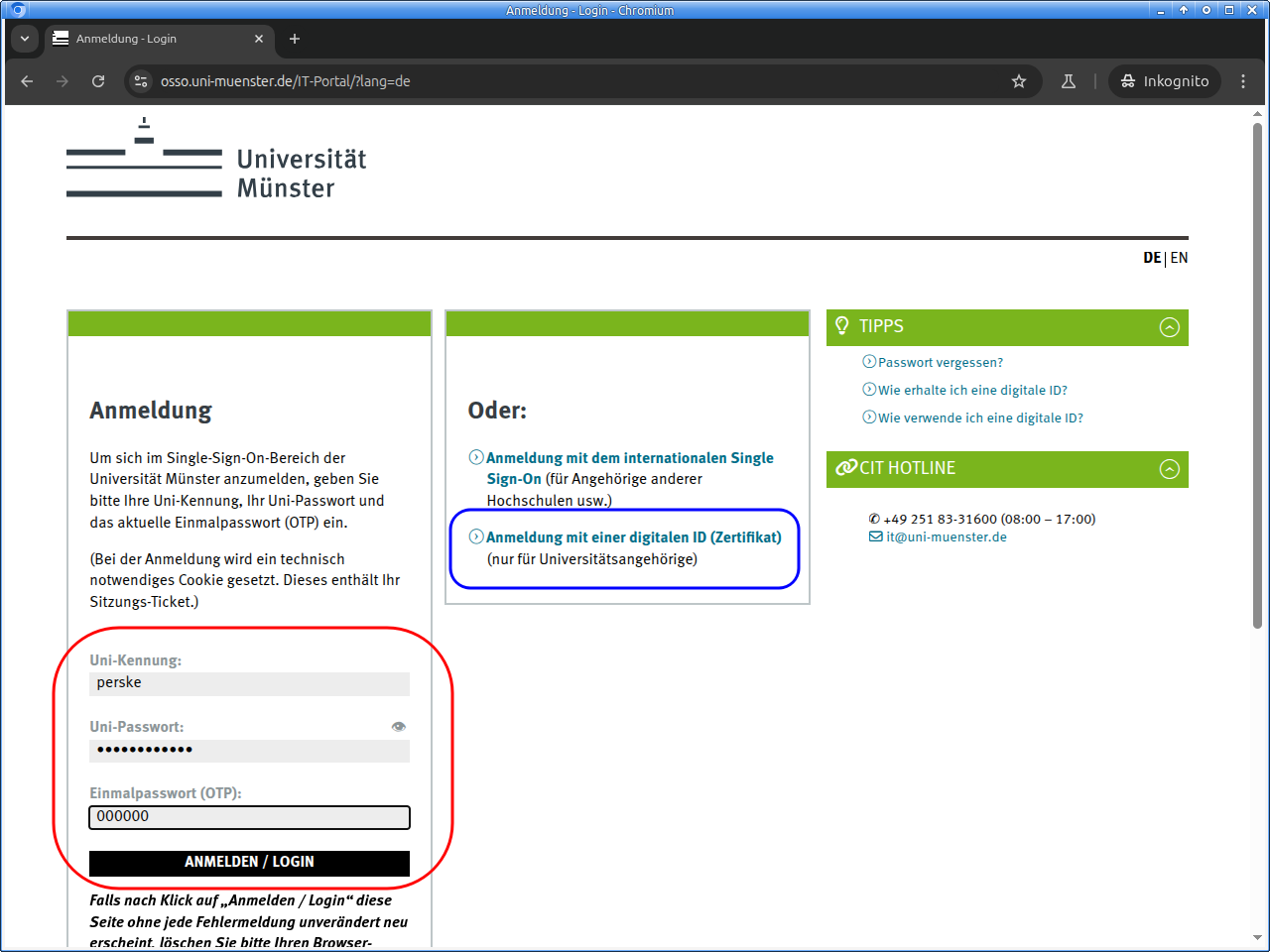
Please log in to the IT portal:
For logging in, usually university ID and university password are used. But if you already own a digital ID (for e-mail and WWW), you can use that:
Important information may appear after logging in to the IT portal.
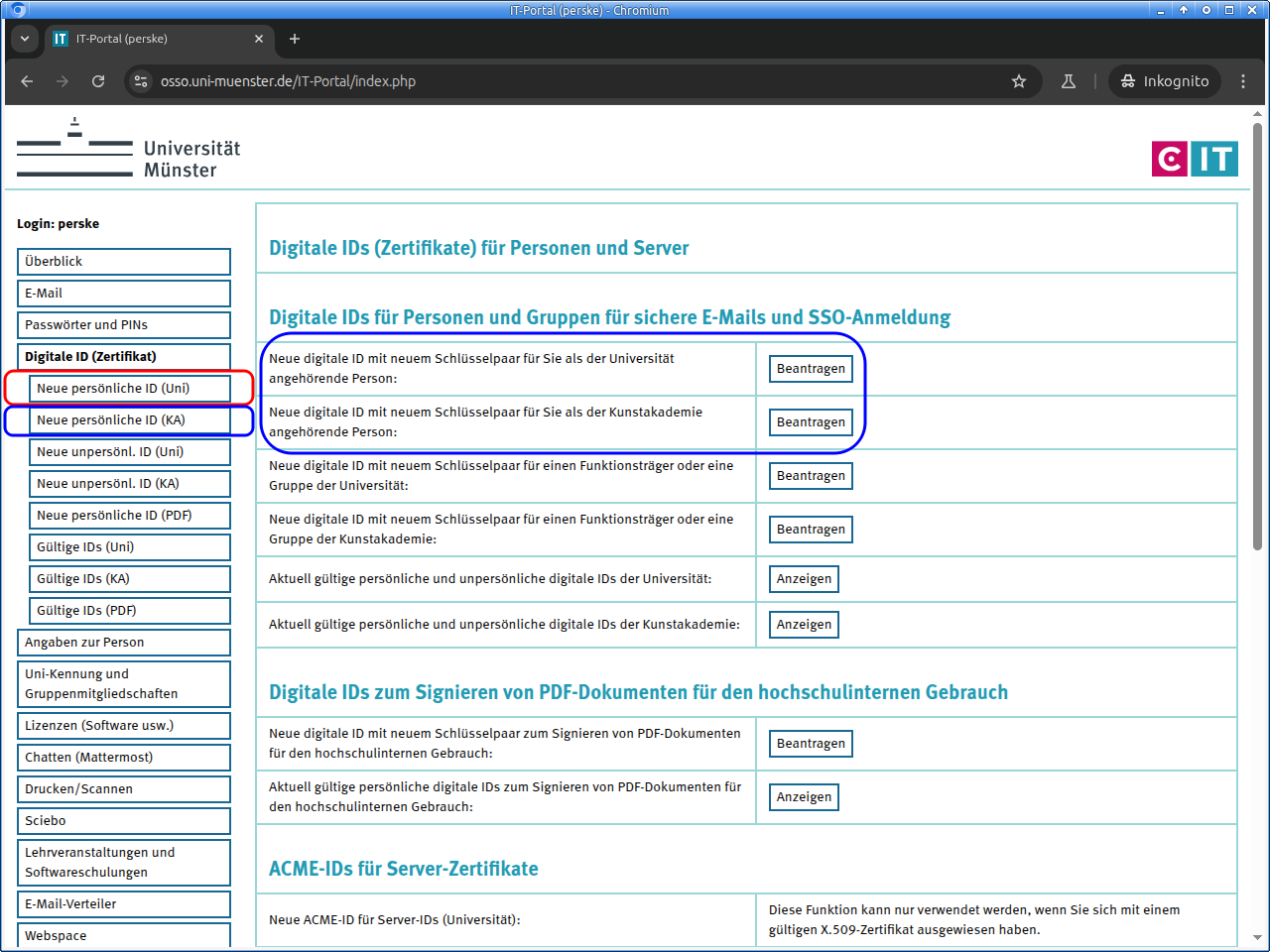
Select the area „Digitale ID (Zertifikat)“ (“Digital ID (certificate)”):
There click on „Neue persönliche ID (Uni)“ (“New personal ID (Uni)”) or in the correct line on „Beantragen“ (“Request”).
If you are responsible for nonpersonal e-mail addresses and would like to request a digital ID for these, click on „Neue unpersönl. ID (Uni)“ (“New nonpersonal ID (Uni)”) instead. Then other, but very similar pages appear.
Members of the Kunstakademie Münster use the buttons with “(KA)” instead of “(Uni)”:
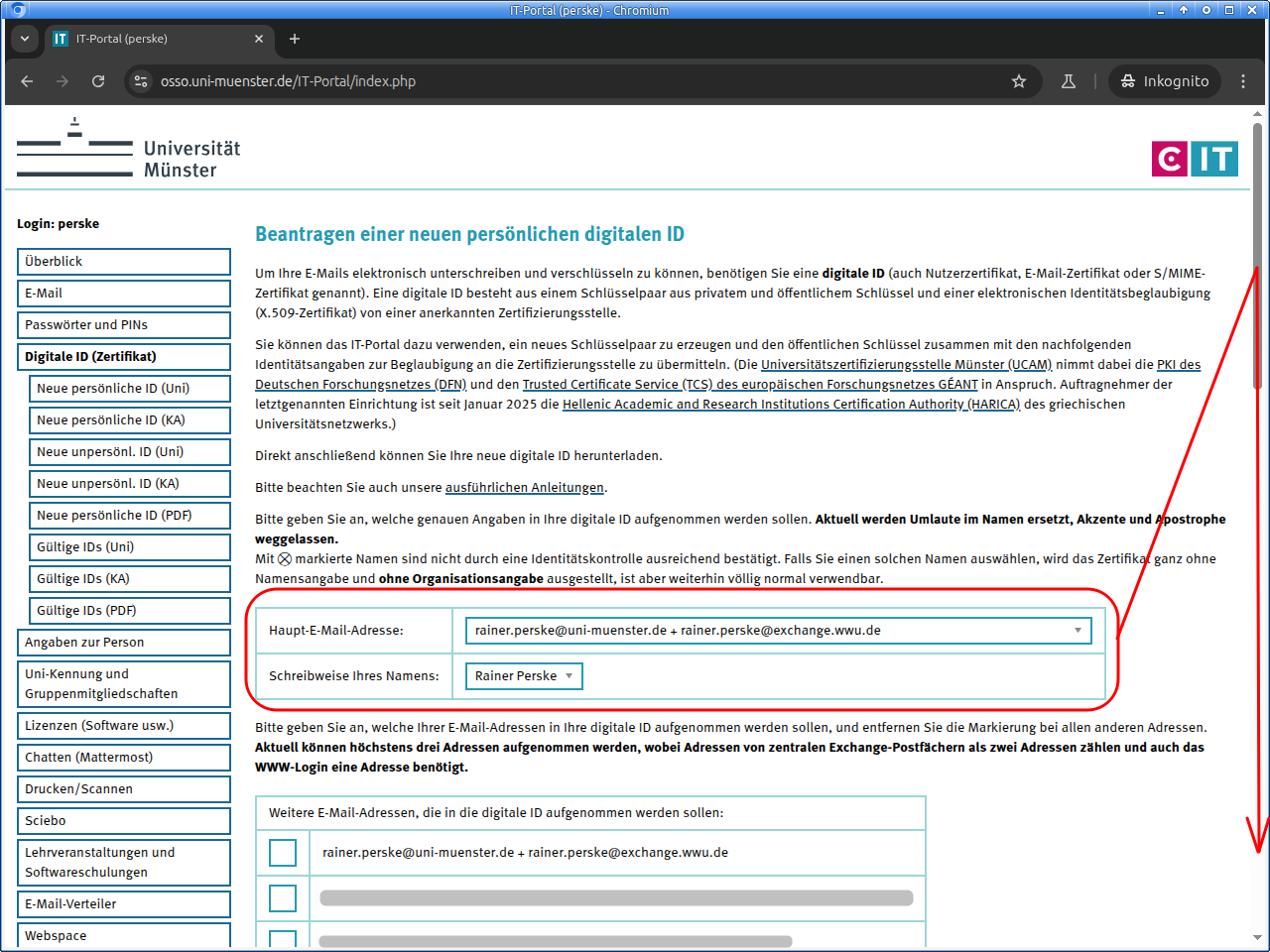
On the next page first regard the detailed notes. Then select what details are to be included into the digital ID:
Possibly you do not want to include all email addresses connected to your personal identity. Then remove the corresponding check marks.
For members of the arts academy corresponding input fields are displayed.
Of course you can get a certificate only if you are willing to incur the corresponding liabilities.
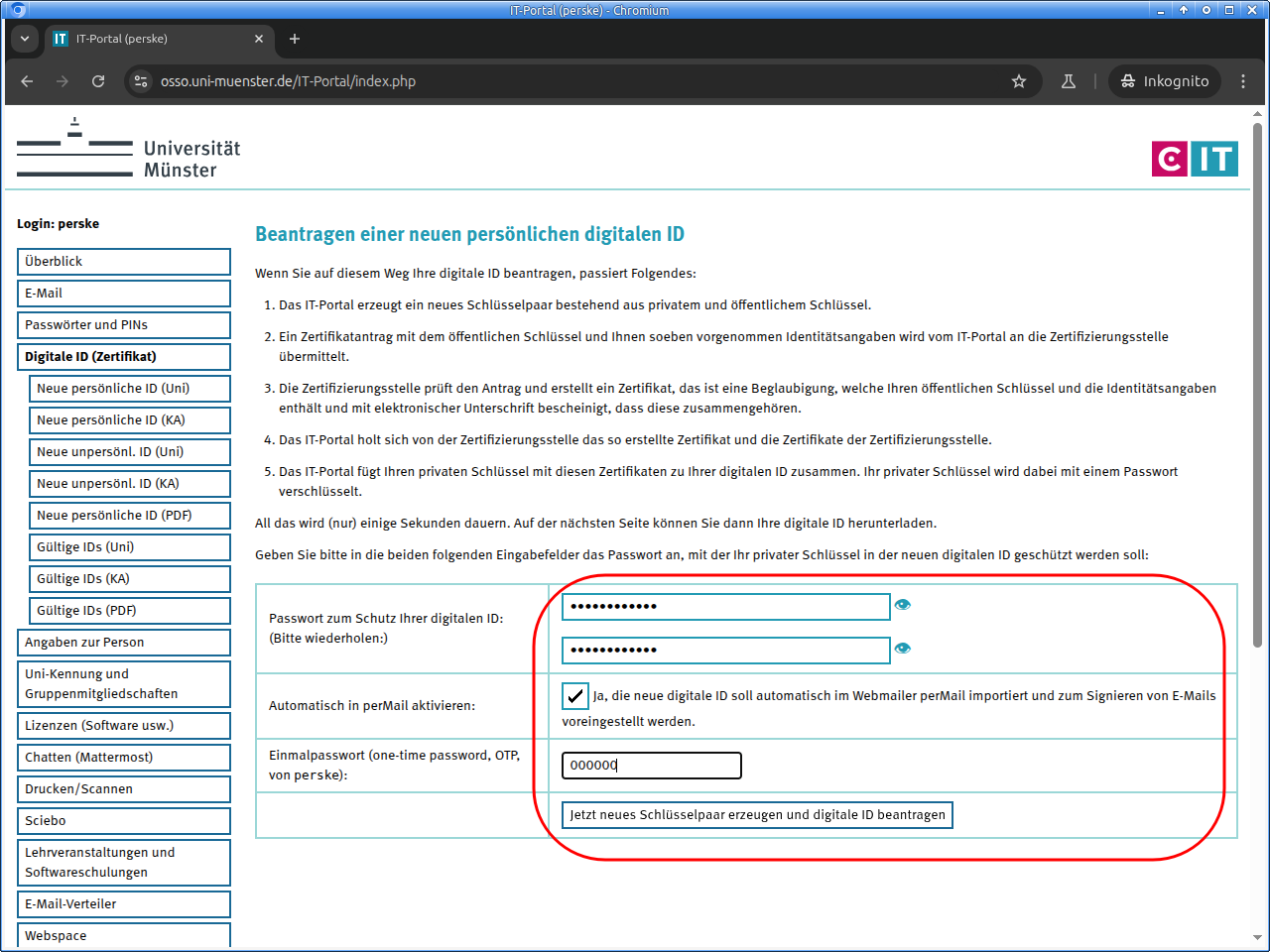
On the next page you will download the digital ID as an PKCS#12 file. This file will be encrypted with a password for security. Please choose a good password and enter it twice.
Please make a note of this password and keep it very carefully!
Nobody can help you if you lose it, not even us!You can also have the new digital ID imported directly into our webmailer perMail.
With a click on the button you then request your new digital ID.
It may now take a few minutes for your certificate to be issued by our service provider, please be patient.
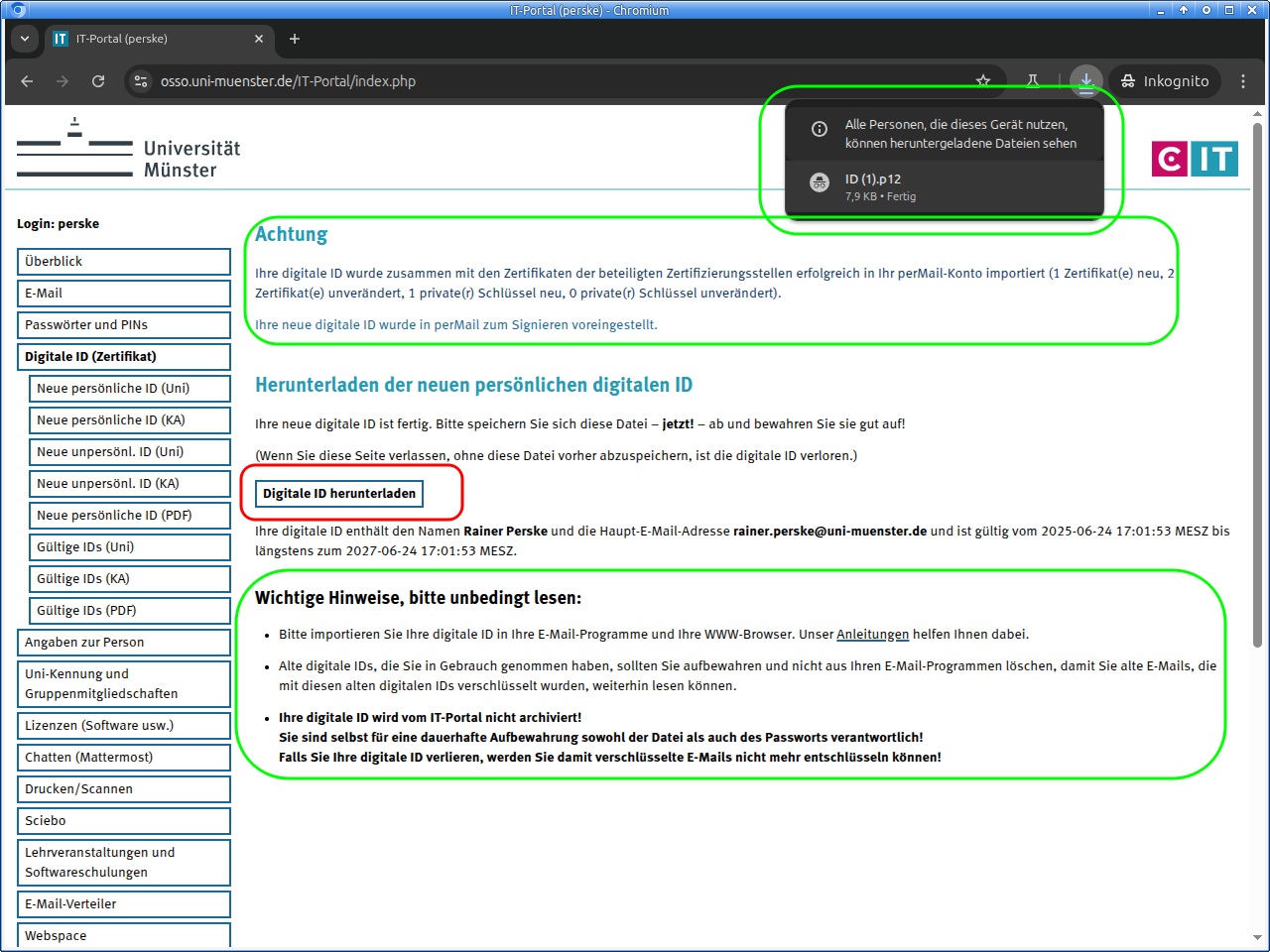
Then your digital ID is ready and, if desired, also set up in the webmailer perMail:
The download of the digital ID should start automatically, but can be also be started manually.
Please save your digital ID carefully!
Once you leave the page, there is no possibility to download the digital ID again!
Please also note the important information!
The further steps are specific to your email and WWW software.
Guides: Import and use digital IDs in email software
These guides describe how to import a digital ID into email software and how to use it:
(Some of these guides show older versions but we are working on it.)
Further guides are still to be created.
If your software is not listed above, you should consult the guide for Mozilla Thunderbird—most email software works the same way.
If there is a manual for the device or software you are using, you should consult it. Look in the table of contents or in the index for key words like “S/MIME”, “certificate”, “PKCS#12”, “sign”, “signature”, „encrypt“.
(Unfortunately the word “signature“ has two completely different meanings in the email context: It can mean both the footer lines usually containing contact information and the cryptographic signature replacing a handwritten signature.)
Guides: Import and use digital IDs in WWW browsers
These guides describe how to import a digital ID into WWW software and how to use it:
(Some of these guides show older versions but we are working on it.)
Microsoft Edge, Chrome, and other software under Windows:
They use the digital IDs imported into Microsoft Outlook
Apple Safari, Chrome, and other software under MacOS:
They use the digital IDs imported into Apple Mail
(We often hear that people have problems with Apple Safari and therefore recommend to use Firefox or Chrome.)
-
Under Settings → Privacy and security → Security → Manage certificates you find a settings pages that is quite similar to the one provided by Mozilla Firefox
Further guides are still to be created.
(Only for special applications) Further guides
These guides only apply to the specified situations.
Only for PHP programming:
Guide: Sending a signed or a signed and encrypted email with PHPOnly for PHP programming:
Guide: Setting up a TLS connection with client certificate authentification with PHP
* General notes on encrypting e-mails
(These notes apply to encrypting, not signing.)
As the successful EFAIL attacks have shown, there are a wide variety of vulnerabilities both in the S/MIME and PGP/MIME protocols themselves and in many implementations.
The flaws in the implementations could or can be fixed, but the fundamental vulnerabilities in the protocol itself are irreparable. (The problem is not so much in the encryption algorithms themselves, but in how they are used in the protocols and how these are realized in the software).
For securing moderately confidential communication without long-term safety requirements, S/MIME may still be sufficiently secure; however, when it comes to truly confidential data, we can no longer recommend exchanging it via e-mail.
Here you should use modern software designed for end-to-end-security from the very beginning and thoroughly analyzed and recommended by experienced cryptologists, for example, the messenger „Signal“.